Syhunt Breach: Getting Started
The information in this document applies to version 6.9.14 of Syhunt Breach.
Table of Contents
How to perform a domain check
Syhunt Breach can help you map data leaks on the surface, deep and dark layers of the web that affect your organization, including file and credential exposures, and allows you to compare the privacy and security score of your Internet domains based on their track record and testing results.
Follow along with this guide to learn how to perform a domain check and generate a security report.
 Make sure you meet the pre-scan requirements and are properly authorized to perform the check against the target domain.
Make sure you meet the pre-scan requirements and are properly authorized to perform the check against the target domain.
- Launch Syhunt Hybrid and click the Syhunt Breach icon or the Manage button in the welcome page.
- If this is the first time you access the Breach Scanner, the Breach setup will open and allow you to install its dependencies.
- Enter the domain address you want to check. Wait a few seconds until the check is complete.
- Right click the domain in the list of domains and click the option List All Breaches.
After it finishes loading, you can click Generate a Report to save the results as a HTML report or any other prefered format.
How to perform a domain check via command-line
- Go to the directory Syhunt is installed using the command prompt.
- Use the following command-line:
scandark [target] -hm:[a huntmethod]]
// Example:
scandark mydomain.com
Syhunt scandark tool reports are automatically generated and saved unless the -nr parameter is provided. You can also open the session by launching Syhunt and using the  Menu -> Past Sessions option.
Menu -> Past Sessions option.
The following parameters can be provided when calling the scandark tool, all of which are optional:
| Parameter | Description | Default Value |
| sn:[name] | A session name that must be unique. If omitted, an unique ID will be generated and assigned | auto generated ID |
| hm:[name] | the Hunt Method to be used during the scan. If omitted, the default method will be used | darkplus |
| nr | Disables the report generation after scanning | |
| or | Opens report after generation | |
| er | Emails report after generation | |
| tk:[trackername] | Sends breaches to a tracker after scanning. Can be combined with the -pfcond parameter | |
| tk2:[trackername] | Same as above | |
| tk3:[trackername] | Same as above | |
| rout:[filename] | Sets the report output filename and report format | Report_[session name].html |
| rtpl:[name] | Sets the report template | Standard |
| xout:[filename] | Sets the export output filename and report format | Export_[session name].xml |
| xout2:[filename] | Sets a second export output filename and report format | Export_[session name].xml |
| pfcond:[condition] | Sets a pass/fail condition to be reported | |
| nv | Turn off verbose. Error and basic info still gets printed | |
| tml:[time] | Sets the maximum scan time limit (eg: 1d, 3h, 2h30m, 50m) | No limit |
| about | Displays information on the current version of Syhunt | |
| help (or /?) | Displays the list of available parameters |
How to assign special domain properties
The Domain preferences screen allows you to assign special properties to a domain which can extend the Dark Web analysis about the domain. If before starting a scan you checked Edit domain preferences before starting scan, the Domain Preferences screen will open.
Under Extended Analysis, click the Properties button. You can now enter one or more property lines. The following is a list of accepted property lines:
| creg:[XXNUMBER] | Allows to associate a company registration number with the domain (eg: UK08888880) |
Obtaining access to the leaked information
After purchasing a copy of the full-featured Syhunt Breach Scanner, you must select between the online mode or the offline mode:
- The online mode: auto-downloads available leak information (“encrypted dumps”) related to your Internet domain from the cloud. The leaked information is only stored in the cloud if you select this mode.
- The offline mode: allows you to request and obtain a file copy of the encrypted dump through a secure channel (PGP, email, etc) and import the file into Syhunt Breach. The leaked information is not stored in the cloud if you select this mode.
To protect identified leaked information of its customers, Syhunt adopted various strong security measures including segregating and securing data per domain with unique encryption passphrases. This allows Syhunt to use external cloud partners to store the identified leaked information securely without the risk of exposing any consolidated data leak details of its customers to unauthorized third-parties, such as the list of leaked credentials, file exposure details, leak download addresses among other leak-related details. In addition to file encryption, Syhunt adopts partially masking and bCrypting of leaked passwords with a high cost factor within the encrypted files.
Because the encryption passphrase is different for each domain, you can only download or import dumps related to your authorized Internet domains.
The Breach Score
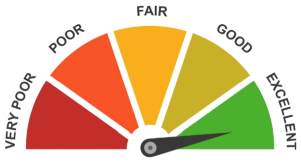
The Syhunt Breach Score is a score of an Internet domain based on publicly available Internet information about its privacy and security track record which is dynamically calculated by the Syhunt Breach software at the end of a Dark Web Scan Plus check. The Breach Score varies from Very Poor to Excellent and takes into account various information from the last 5 up to 15 years.
Today the Breach Score covers over 58 million domains from all over the globe, including regional domains from North America, South America, Europe, Africa, Asia and Oceania, and international domains.
Using the Community version, you can get an idea of what kind of information is being taken into account by Syhunt Breach to calculate the score of your domain or domains. By obtaining a trial copy of the full-featured Syhunt, you can also view the current score of your domain or domains together with limited information about any identified leaks or breaches.
When calculating a score of any domain, the following kind of public information is taken into account by Syhunt Breach:
- Exposed information by ransomware group sites on the dark web
- Exposed information by hackers through hacking forums and online communities
- Information about data leaks on the surface web
- Information on past security incidents (such as defacements and etc.) on the surface web
Score Comparison Feature
The professional version of Syhunt Breach allows an user to compare the score of a domain with other subsidiaries of the same company and with third-parties such as partners of an organization.
How to assign domains for comparison
The Domain preferences screen allows you to assign domains for comparison. If before starting a scan you checked Edit domain preferences before starting scan, the Domain Preferences screen will open.
Under Extended Analysis, click the Domains button. You can now enter one or more domains.
Terms
The Syhunt Breach Score is provided “AS IS” and without warranties of any kind either express or implied. For more details, please read the Syhunt EULA.
Due to active targeting by hostile foreign actors, access to the scores of .mil and .gov domains specifically have been restricted to American military and government personnel and require a special license. Country specific .mil and .gov domains also require a special license to calculate and view their scores and detailed leak information.
Customizing the Report
Before saving a report, you can change the language and add a logo that will be included with any generated reports from now on:
- Click the Edit Report Preferences button in the toolbar. The Report Preferences dialog will open.
- Enter the image URL containing the logo
- Select a desired output language.
- Click OK to save the preferences.
Now when you generate a report, it will contain your organization logo instead of Syhunt's logo.
Pre-Scan Requirements
 This software should be used only by system administrators (or other people in charge). It should not be used to scan domains outside of your direct control.
This software should be used only by system administrators (or other people in charge). It should not be used to scan domains outside of your direct control.
- If you need to scan a domain outside of your direct control, it is recommended that you obtain a written permission from the domain's owner or administrator.
- Make sure you meet the Internet connection requirements.
- You must read and agree with the Syhunt EULA before launching any scans.
- Before executing your first scan, you must have the proper region dependencies installed:
- On Windows, the Syhunt Web Scanner setup will execute before the first scan and allow you to install the dependencies.
- On Linux, you can install the dependencies by calling the syget command:
- If you have an Americas or international domain (.com, .net, .us, .ca, .ar, etc): ./syget --install_icyd_americas
- If you have an Americas - Brazilian domain (.br): ./syget --install_icyd_brasil
- If you have an Europe, Asia, Africa or Oceania regional domain (.uk, .pt, .jp, .au, etc): ./syget --install_icyd_eastern
- If you have a Government or military domain (.gov or .mil): ./syget --install_icyd_govmil
System Requirements
Syhunt Hybrid (including its Community Edition) can be installed on 64-bit versions of Windows or Linux, but it is able to analyze applications designed for any target platform, including Android, Apple iOS and macOS, BSD, Linux, Windows, Solaris and Unix, independently of the platform it is executed from.
- 4GB of available RAM (8GB recommended)
- 2GB of free disk space*
- Internet Connection (recommended for code scans and dynamic scans and some features)
- One of the following compatible 64-bit operating systems:
- Windows 10 or 11, or Windows Server 2012 to 2022 (x64 or ARM64). On Windows Server, it is important to ensure that you have the WebView2 Runtime installed. If the WebView2 Runtime is not installed, Syhunt will issue a warning when launching its user interface. You can find it in the Evergreen Standalone Installer.
- Make sure you have Edge preloaded on system startup. On Windows 10, Edge preload is already a default system setting. On Windows Server, you have to enabled the Edge preload manually. On Windows 11, our tests showed that disabling the Edge preload would not make any difference.
- Ubuntu Server or Desktop 18 or higher
- CentOS 7 or 8 (Minimal or Everything)
- Any unofficially supported OS**, like a Linux distribution such as the ones listed below, or macOS Big Sur or higher (Intel).
- Windows 10 or 11, or Windows Server 2012 to 2022 (x64 or ARM64). On Windows Server, it is important to ensure that you have the WebView2 Runtime installed. If the WebView2 Runtime is not installed, Syhunt will issue a warning when launching its user interface. You can find it in the Evergreen Standalone Installer.
- (Optional) GIT on Linux/macOS or GIT for Windows (optional for GIT repository scans)
- Java or Java Headless installed on Linux/macOS
- If native binary is not available for your specific OS type or distribution yet, Wine64 Stable (3, 4 or 5) is required to be installed.
- (Optional) Java 8 or higher (optional for Android APK file scan)
- (Optional) Python 3.7.0 or higher, Selenium module and Chrome browser version 109 or higher (optional for extended scripting capabilities)
- (Optional) OpenAI API key to enable AI-powered features
* This does not include the space required to save scan session data, which varies depending on the website or source code being analyzed and the scan frequency.
** Unofficially supported OS: means that while the product has been successfully tested and the installation process has been documented, Syhunt does not provide technical support or assistance for issues related to the product's performance on that particular OS. If you choose to use the product with an OS that is not officially supported, you may encounter compatibility issues, errors, or bugs. Therefore, it is always recommended to use a supported OS to ensure optimal performance and compatibility with the product.
Compatible Linux Distributions
Officially Supported:
Ubuntu Server/Desktop 18.10 and later
CentOS 7.7 and later (Minimal or Everything)
Unofficially (Successfully Tested):
Kali Linux 2019 and later
Parrot OS 4.1, 4.7 and later
Debian 9.11 and later
Linux Mint 19.2 and later
OpenSUSE Leap 15.1 and later
Fedora 32
MX Linux 19.1 and later
KDE Neon 2020.03 and later
Deepin 15.9
Manjaro 19
Arch Linux 2019 and later
Unsupported:
Elementary OS 5.1 (Successfully Tested), 5.0 (Unsupported)
CentOS 6.1 (Successfully Tested)
Solus 4.1 (Unstable)

For additional product documentation, visit syhunt.com/docs
