This page features a few common examples of vulnerable PHP code that Syhunt can find and PHP scanning capabilities that are available in the product.
Note: This page covers results obtained via SyHybridCS. Syhunt Suite's graphical interface and reports offer identical but more detailed results.
Table of contents
Intelligent PHP Scanning
Input Filtering Analysis
Syhunt performs intelligent PHP code scanning and includes the ability to identify the lack of input filtering:
<? $a = htmlentities($_GET['a']); $b = $_GET['b']; $c = $_GET['c']; $d = htmlentities($b); echo ($a); // safe echo (htmlentities($b)); // safe echo ($c); // XSS vulnerability echo ($d); // safe echo (htmlentities($_GET['id']); // safe ?>
The code above is using output filtering but a single variable ($c) is vulnerable to XSS due to lack of filtering. Syhunt scan results for this example code will reveal just the vulnerable code:
Found: 1 vulnerability In /entxss.php (source code, locally), affecting parameter "c", on lines 4,9: Possible XSS Vulnerability
False Negative Examples
Syhunt is not affected by false negatives produced by incorrect code understanding like this one:
<html> <? $name = $_GET['name']; // Comment ?><? echo($name); // XSS 1 ?> <script> document.write('<? echo($_GET['city']); // XSS 2 ?>'); </script> </html>
Could this example code be vulnerable? Yes, it is, but the web application (not designed by us) we used to highlight the code in this page is faulty and mistakenly thinks that:
- The rest of the line 2 after "?>" is a comment.
- The PHP code inside document.write is a string and that it ends when the next
'is found
This image taken from a PHP editor shows what it would be like if the above code was properly assimilated:
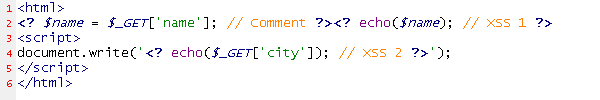
A code scanner could easily make similar mistakes when scanning web applications and analyzing their code, resulting in false negative. But Syhunt does what it should do (correctly understands the code) and detects the flaws:
Found: 2 vulnerabilities In /commentbug.php (source code, locally), affecting parameter "name", on line 2: Possible XSS Vulnerability In /commentbug.php (source code, locally), on line 4: Possible XSS Vulnerability
False Positive Examples
Syhunt will, whenever possible, avoid triggering false positive results. Example - this will not be reported:
<? /* This was a XSS vulnerability. I commented it out echo($_GET['name']); */ $name = $_GET['name']; // echo($name); Same here! ?>
The code above is not vulnerable anymore since it has been commented out. Syhunt scan results for this example code will consequently reveal no flaws:
No vulnerabilities found.
Detection of Vulnerabilities involving Variables
These are difficult to find if there are many code lines. Syhunt is also able to detect them
<html> <?php $name = $_GET['name']; $msg = 'Welcome '.$name; ?> <head> <title><? echo($name); /* XSS 1 */ ?></title> </head> <body> <? echo($msg); /* XSS 2 */ ?> </body> </html>
Syhunt scan results for this example code:
Found: 2 vulnerabilities In /vars.php (source code, locally), affecting parameter "name", on lines 3,4,7: Possible XSS Vulnerability In /vars.php (source code, locally), on line 10: Possible XSS Vulnerability
Shorthand Support
Syhunt includes support for the echo shorthand:
<? $name = $_GET['name']; ?> <?=$_GET['name']; //XSS 1 ?> <?=$name // XSS 2 ?>
Syhunt scan results for this example code:
Found: 2 vulnerabilities In /xss_shorthand.php (source code, locally), on line 4: Possible XSS Vulnerability In /xss_shorthand.php (source code, locally), affecting parameter "name", on lines 2,5: Possible XSS Vulnerability
Support for PHP Inside Script Tags
Suhunt also supports PHP inside <script> tags:
<html> <script language="php"> $d = $_GET['d']; echo($d); // XSS </script> </html>
Syhunt scan results for this example code:
Found: 1 vulnerability In /inscript.php (source code, locally), affecting parameter "d", on lines 3,4: Possible XSS Vulnerability
XSS Detection
See: Cross-Site Scripting (XSS)
Basic Examples
These are very basic XSS examples.
<? echo($_GET['name']); // XSS 1 echo($_POST['name']); // XSS 2 echo($_REQUEST['name']); // XSS 3 ?>
Syhunt scan results for this example code:
Found: 3 vulnerabilities In /xss_basic.php (source code, locally), on line 2: Possible XSS Vulnerability In /xss_basic.php (source code, locally), on line 3: Possible XSS Vulnerability In /xss_basic.php (source code, locally), on line 4: Possible XSS Vulnerability
File Inclusion Detection
See: File Inclusion
Example
<?php $incfile = $_REQUEST['file']; include($incfile.'.php'); ?>
Syhunt scan results for this example code:
Found: 1 vulnerability In /rfi_sample.php (source code, locally), affecting parameter "file", on lines 2,3: Possible File Inclusion Vulnerability
SQL Injection Detection
See: SQL Injection
Example
<? $username = $_GET['username']; $result=mysql_query('SELECT * FROM users WHERE username="'.$username.'"'); ?>
Syhunt scan results for this example code:
Found: 1 vulnerability In /sqli_basic.php (source code, locally), affecting parameter "username", on lines 2,3: Possible SQL Injection Vulnerability
Command Execution Detection
See: Command Execution
Example
<? $cmd = $_GET['command']; passthru('SomeApp.exe '.$cmd); ?>
Syhunt scan results for this example code:
Found: 1 vulnerability In /rce_basic.php (source code, locally), affecting parameter "command", on lines 2,3: Possible Command Execution Vulnerability
Additional Vulnerability Classes & Variants
While Syhunt contains checks for many vulnerability variants, this page doesn't cover them all. In addition to the vulnerability classes covered in this page, Syhunt detects HTTP Response Splitting, arbitrary file manipulation and weak validation issues.