Most of the improvements described on this page apply as well to the Community Edition of Syhunt. If you prefer to read only what's new in Syhunt Community, visit here.
What's New in Syhunt 6.9.17 (August 8, 2022)


Syhunt Hybrid 6.9.17 adds dashboard integration and false-positive free checks
We are happy to announce the release of Syhunt Hybrid 6.9.17. which adds the ability to automatically connect to security dashboards like OWASP DefectDojo and Faraday to submit DAST and SAST scan results. The security dashboard allows teams to keep track of vulnerability alerts generated by Syhunt and manage their attack surface from a single, central place while automating and accelerating key steps of their application vulnerability management. The new dashboard integration can be enabled in seconds and with just a few clicks and input or if you prefer, through the CLI, with a few commands, as explained in the documentation below.
In addition to the new integration features, Syhunt 6.9.17 comes with time-based injection checks that now have a 0% false positive rate - time-based checks usually generate a high number of false positive in other tools, so this represents a milestone and breakthrough that complements the already highly accurate Syhunt engine. The false-positive free enhancement applies to a large number of checks in Syhunt Dynamic, including: Code Injection, Expression Language Injection, NoSQL Injection, Remote Command Execution and SQL Injection checks.
- Integrating Syhunt with DefectDojo (available)
- Integrating Syhunt with Faraday (coming next)
Improvements in Version 6.9.17
- Added integration with two appsec dashboards: DefectDojo & Faraday. Syhunt is now able to automatically submit vulnerabilities to the above mentioned dashboards.
- The CLI parameters -etrk and -si have been deprecated and will be removed in the future. Please use the new -tk, -tk2 or -tk3 parameters instead. For example, -etrk:trackername -esbj:"My Subject" should be replaced with: -tk:"trackername?subject=My Subject"
- Removed the parameters -er and -esbj from the CLI. The email subject must now be passed using the -tk parameter as explained above.
- Added short alias for pass/fail conditions: low, medium and high.
- Improved time-based injection checks, now with 0% false positive rate for Code Injection, Expression Language Injection, NoSQL Injection, Remote Command Execution and SQL Injection.
- Added an option to view a list of breached subdomains and their status in Syhunt Breach.
- Additional spider optimizations.
- Allow to select trackers to be notified from the scheduled scan preferences dialog.
- Allow to enable fail condition with a single click from the scheduled scan preferences dialog.
- Simplified report and export generation.
- Improved scheduled scan preferences dialog.
- Improved results for C and Java code scan of larger codebases using default scan method.
- Improved setup application.
- Improved accuracy and simplified SSL/TLS check in Dynamic.
- Additional entry point detection for JS-based applications in Dynamic.
- Faster injection checks during application scan.
- Updated OpenSSL binaries.
- Fixed: long delay happening sometimes when applying an update.
- Fixed: long delay when loading Past Sessions screen or generating a report after scanning a very large source code base with Syhunt Code.
- Fixed: XSS false positive cases (affecting check #207 and #228) in Dynamic.
- Fixed a hardcoded password false positive.
Happy bug and breach hunting!
What's New in Syhunt 6.9.15 (June 17, 2022)
Syhunt Hybrid 6.9.15 adds Fastjson RCE vulnerability detection and more
Today we release Syhunt Hybrid 6.9.15.1 which adds the detection of the Fastjson RCE vulnerability (CVE-2022-25845) to the Syhunt Code tool. The remote code execution vulnerability affects versions 1.2.80 and older of Fastjson and is caused by the default AutoType restriction which can be bypassed under specific conditions. An attacker could exploit this critical vulnerability to perform remote code execution on the target machine.
For customers performing regular scans, the new release of Syhunt fixes a delay that occurred when loading the Past Sessions screen and when generating reports with comparison information.
Improvements in Version 6.9.15
- Added checks for the high severity Fastjson remote command execution vulnerability (CVE-2022-25845, CVSS score: 8.1) to Syhunt Code.
- Added additional alerts related to the Log4J vulnerabilities disclosed last year (CVE-2021-44832 and CVE-2021-45105) to Syhunt Code.
- Significantly faster Past Sessions loading.
- Added additional spider optimizations in Dynamic.
- Improved start URL handling in Dynamic (Angular applications).
- Run once option in Scheduler moved to the Advanced tab.
- Fixed: a false positive problem involving directory traversal and remote command execution and assets with input.
- Fixed: Long waiting when loading past sessions list when a large number of sessions has been archived.
Happy bug and breach hunting!
What's New in Syhunt 6.9.14 (June 2, 2022)
Syhunt Hybrid 6.9.14 improves DAST, SAST and DWET capabilities
We are happy to announce the release of Syhunt Hybrid 6.9.14 which improves and expands the product tools Syhunt Dynamic, Syhunt Code and Syhunt Breach. The new release comes with a revamped Breach user interface, accelerated Breach scans, automatic issue submission, and the long-awaited ability to ignore specific vulnerability alerts when performing DAST and SAST scans, among other enhancements.
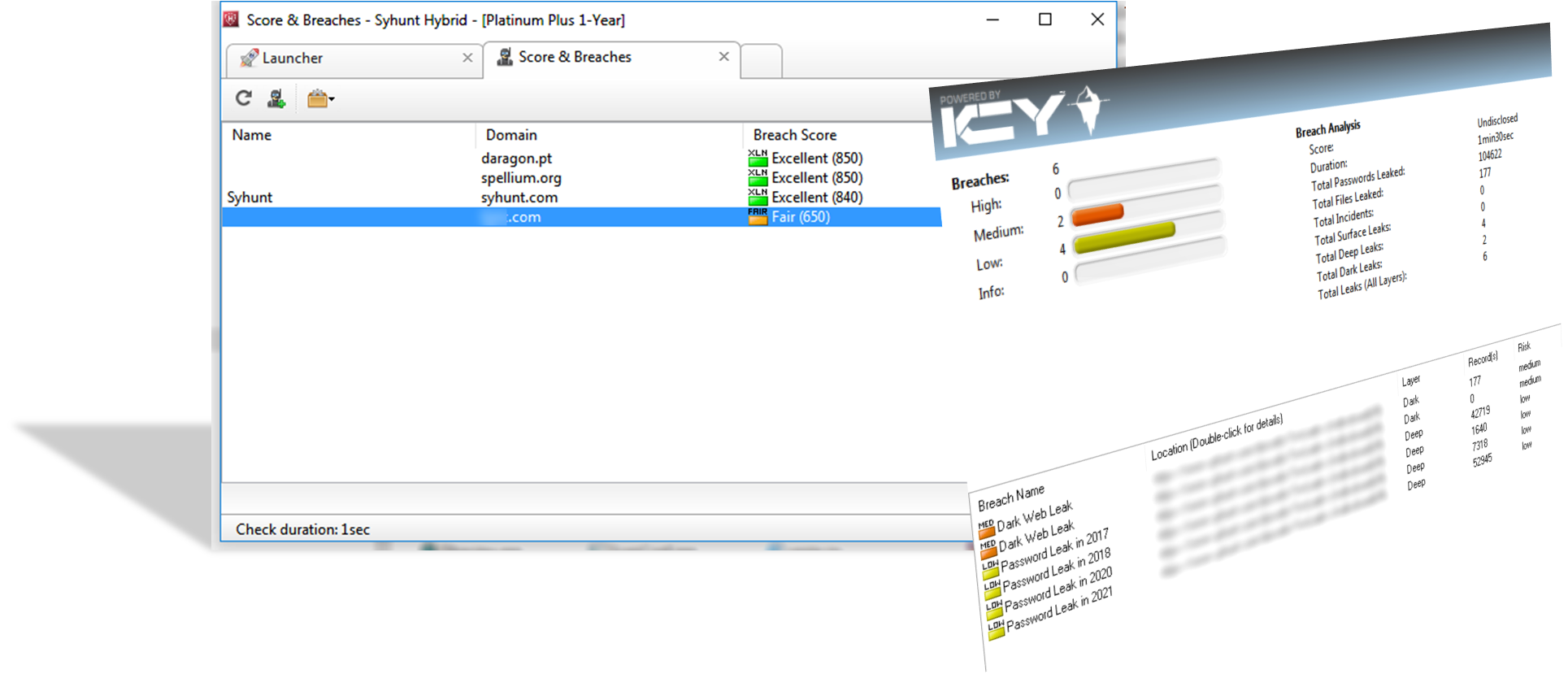
Improvements in Version 6.9.14
- Breach: added support for concurrent scans and various user interface and experience improvements
- Breach: significantly faster scans (from 1m18sec against a .com domain to around 23sec and 3sec after first scan).
- Breach: added the breach score to the monitored targets list.
- Integrations: added the ability to automatically submit a brief of the identified vulnerabilities to issue trackers such as GitHub or GitLab through CLI, CI/CD pipeline and Powershell. More
- DAST: Minor improvements to the handling of Start URLs in Syhunt Dynamic.
- DAST: vulnerabilities can now be ignored by their ignore ID. More
- DAST: Added various checks for JBoss/Wildfly vulnerabilities.
- SAST: Added ability to ignore vulnerabilities by creating .vulnignore file within repositories or code directories. If a Ignore ID shown in report is added to the .vulnignore file, then the vulnerability will not be reported again. More
- SAST: Improved detection of Log4Shell vulnerability in Java applications.
- SAST: fixed a few false positives in Java applications (three cases reporting Information Disclosure, Log Forging and XML Injection)
- Improved license management.
- Fixed: session import option not working from session manager.
Happy bug and breach hunting!
What's New in Syhunt 6.9.13 (April 8, 2022)
Syhunt Hybrid 6.9.13 adds Spring4Shell vulnerability detection, expands SCA and DWET capabilities
Syhunt's breach hunting tool (formerly IcyDark) is now Syhunt Breach.
Last week we all learned about the critical Spring4Shell (CVE-2022-22965) vulnerability that affects Spring apps and that when exploited by attackers may result in remote command execution. Today we release Syhunt Hybrid 6.9.13 which adds the detection of the Spring4Shell vulnerability to Syhunt tools, Syhunt Dynamic, Syhunt Code and Syhunt Forensic (formerly Insight). In addition to this critical DAST check, Syhunt 6.9.13 expands its SCA component in Syhunt Code to cover the Spring4Shell vulnerability and adds 260 new ransomware related leaks to its Syhunt Breach tool (formerly IcyDark), reaching a total of 3103 ransomware group leaks.
Expanding SCA Capabilities
In 2019, Syhunt added the detection of outdated vulnerable JavaScript code to Syhunt Code 6.6, a feature of SCA (software composition analysis) tools. This made Syhunt Code go beyond SAST (static source code analysis). In December 2021, the SCA component, known as Syhunt Code Composition, has been updated to cover Log4J vulnerability and now it has been updated to detected the Spring4Shell vulnerability as well. Syhunt Code Composition checks for vulnerable Spring, SpringBeans, SpringBoot, SpringWebFlux and SpringWebMVC packages and currently is available at no additional cost as part of Syhunt Code.
Product Name Changes
Today we are also announcing a few product name changes: the Syhunt IcyDark product will now be called Syhunt Breach and the Syhunt Insight log scanner will now be called Syhunt Forensic. The name change will more accurately reflect the nature of the product which expanded its coverage to support not only dark web breach hunting, but also breach prevention, forensic analysis and on-demand services through Syhunt Hybrid's console. Despite the name changes affecting the mentioned products, Syhunt's dark web monitoring division will continue to be called Syhunt Icy.
The old product names and the corresponding new names
| Syhunt Insight | -> | Syhunt Forensic |
| Syhunt IcyDark | -> | Syhunt Breach |
| Syhunt IcyScore | -> | Syhunt Breach Score |
Improvements in Version 6.9.13
- Added 260 new ransomware related leaks to Syhunt Breach, reaching a total of 3103 ransomware group leaks
- Added 69 additional vulnerability checks for ASP.NET apps in Syhunt Code, covering various vulnerability categories.
- Added integration with DefectDojo dashboard
- Added check for Spring4Shell (CVE-2022-22965) vulnerability to Syhunt Dynamic.
- Added checks for Spring4Shell vulnerability to Syhunt Code Composition: checks for vulnerable Spring, SpringBeans, SpringBoot, SpringWebFlux and SpringWebMVC components.
- Added checks for web backdoors related to Spring4Shell to Syhunt Dynamic.
- Added checks for Spring4Shell scans to Syhunt Forensic log scanner.
- Added a new hunt method called Spring4Shell, which allows to scan specifically for the Spring4Shell vulnerabilities in Syhunt Dynamic and Code. This method is also available through the CLI.
- Improved Debug Parameters check in Syhunt Dynamic.
- Make it easier to enter business registration number in domain preferences screen.
- Improved session and token management in Syhunt Dynamic.
- Improved form handling in Syhunt Dynamic.
- Improved crawling in login situations.
- Optimized scan against vulnerable targets in Syhunt Dynamic.
- Improved PHPInfo detection in Syhunt Dynamic.
- Added detection of weak session ID in Syhunt Dynamic.
- Upgraded GitLab JSON format to version 14.0.4.
- GitLab compatible JSON export can now be generated by providing output filename with double extension .dast.json or .sast.json.
- Setup binaries for Windows are now signed with Syhunt's code certificate.
Happy breach hunting!
What's New in Syhunt 6.9.12 (February 22, 2022)
Syhunt Hybrid 6.9.12 adds GitHub Actions integration and simplifies CLI
In the recent past, Syhunt announced integration with various systems, such as Azure DevOps, GitLab, TFS, Jenkins and JIRA, and GitHub Issues. Now we release Syhunt Hybrid 6.9.12 which adds integration with GitHub Actions and other user-requested enhancements, as well as simplifies the product's command-line interface. The new release makes it easier to launch SAST and DAST scans through the CLI maintaining backwards compatibility for launchers and callers in use, and allows the user to define a time limit for scans by specifying a number of days, hours or minutes. Integration with GitHub Actions is now officially supported and has been documented online, allowing Syhunt's application security scan tools to be integrated into continuous delivery pipelines created using the platform.
New Option: Time Limit
Syhunt 6.9.12 adds an option that allows to limit the scan time of Dynamic, Code and IcyDark scans. When the time limit is reached during a scan, the scan is automatically aborted.
- Through Syhunt's UI: Set the value in the Advanced tab of the Dynamic Preferences dialog.
- Through the Scheduler UI: Set the value in the Advanced tab of the Scheduled Scan preferences dialog.
- Through CLI: Use the -tml option as described in the CLI documentation.
- Through Lua, REST API, GitHub, GitLab or Powershell: Pass the timelimit parameter to the scan function as described in the integrations documentation.
- Through Jenkins: Pass the timeLimit parameter to the scan function as described in the Jenkins integration documentation.
CLI Improvements
- Added new variables that can be used in report file names:
{$DT}(current date and time),{$DD}(current date) and{$TM}(current time) - Available through CLI and Scheduler - Removed the -gr CLI parameter. Now reports are generated by default.
- Added the -nr parameter which allows to disable report generation
- Removed the -gx CLI parameter. Exports are generated if -xout or -xout2 are provided.
Additional Improvements
- Added new checks for outdated Nginx.
- Improved: the Syhunt Hybrid's user interface now saves settings to the disk immediately after closing the preferences dialog (unless the Cancel button is pressed).
- Improved: perform Denial-of-Service option moved from Start Dynamic Scan dialog to the site preferences dialog.
- Fixed: technology version disclosure being added to specific compliance violation items.
- Fixed: error after setting improper and overly big maximum response size in Dynamic preferences.
- Fixed: a failure when performing NTLM authentication with Syhunt Dynamic.
- Fixed: a false positive in Syhunt Dynamic related to a JSON error response.
Happy bug hunting!
What's New in Syhunt 6.9.11 (December 17, 2021)
Syhunt Hybrid 6.9.11 adds Log4Shell vulnerability detection
Update (December 28, 2021): Our alert about a new RCE vulnerability in Log4J 2.17.0, already detected by Syhunt 6.9.11.4. Read more
Since the public disclosure of the severe risk Log4Shell (CVE-2021-44228) vulnerability that affects Java apps, we have worked to prepare a robust Syhunt update to our DAST, OAST, SAST and FAST capabilities that adds detection of the Log4Shell vulnerability. Today we released the 6.9.11 version of Syhunt Hybrid, which adds the new detection capabilities. Syhunt recommends organizations to perform immediate review and actions which are absolutely necessary in order to fully secure their web server and applications against the vulnerability that when exploited by attackers may result in remote command execution.
Organizations must make sure they do not have any instances of vulnerable versions of the Log4J framework in production within their servers and applications. The Log4Shell vulnerability happens when input is passed to a logging function of a server that uses a vulnerable Log4J framework version. Previous releases of the Syhunt Code scanner warned about user input being passed to the Log4J logging functions, which would be identified as a log forging vulnerability. Depending on how you addressed such instances through input validation or filtering, you may have inadvertently hardened your application against Log4Shell attacks, but you should still re-scan your apps with the latest Syhunt version and patch Log4J instances.
Log4Shell Detection Capabilities
Syhunt Hybrid 6.9.11 adds a new hunt method called Log4Shell, which allows to scan specifically for the Log4J vulnerabilities using Syhunt Dynamic or Syhunt Code. This method is available both through the Syhunt Hybrid GUI and CLI. In addition to this, our web server log scanner now detects Log4Shell attack attempts. Read below about the new capabilities.
- Through SAST: Increased the severity level of Log Injection vulnerabilities when scanning Java source code with Syhunt Code, allowing you to validate and filter input before passing to the Log4J logging functions. Please note that you should still locate and update your vulnerable instances of the Log4J framework.
- In addition to the above, version 6.9.11 adds the detection of the vulnerable Log4J-Core JAR files to Syhunt Code, allowing you to locate the versions of the framework vulnerable to CVE-2021-44228 within code directories and repositories.
- Through FAST: Added the detection of Log4Shell injection attempts to the Syhunt Insight log analyzer.
- Through DAST and OAST: Added the detection of the Log4Shell vulnerability on Windows and Unix environments through injection to Syhunt Dynamic. The JNDI Exploit server is used to augment the DAST scan, interoperating with Syhunt's Signal OAST service. Professional penetration testers can enable this feature by following the guide Syhunt Dynamic: Log4Shell Detection.
Please note that the Community edition of Syhunt Dynamic does not comes with the new Log4Shell detection capabilities only supported by the full-featured version of Syhunt Hybrid or Dynamic.
Additional Improvements
- Added Bearer and Digest (MD5/SHA256/SHA512) authentication support through GUI and CLI.
Happy bug hunting!
