What's New in Syhunt 6
October 10, 2017
After a year of intense research and development, we're very proud to release version 6.0 of the Syhunt Hybrid application security testing suite. With its huge list of updates, the new version marks its most drastic evolution yet and a major overhaul of both its scan engine and user interface, adding advanced fingerprinting capabilities, enhanced spidering, injection, browsing and code scan capabilities, and a large number of new and improved checks.
Most of the improvements described on this page apply as well to the Community Edition of Syhunt released simultaneously today. If you prefer to read only what's new in Syhunt Community, visit here.
Revamped Hybrid User Interface
The new release adds the display of Hybrid, Dynamic and Code detailed scan statistics and progress both to the user interface and the command-line tools, and restores the site tree, implemented from scratch with the level of attention that it demanded.
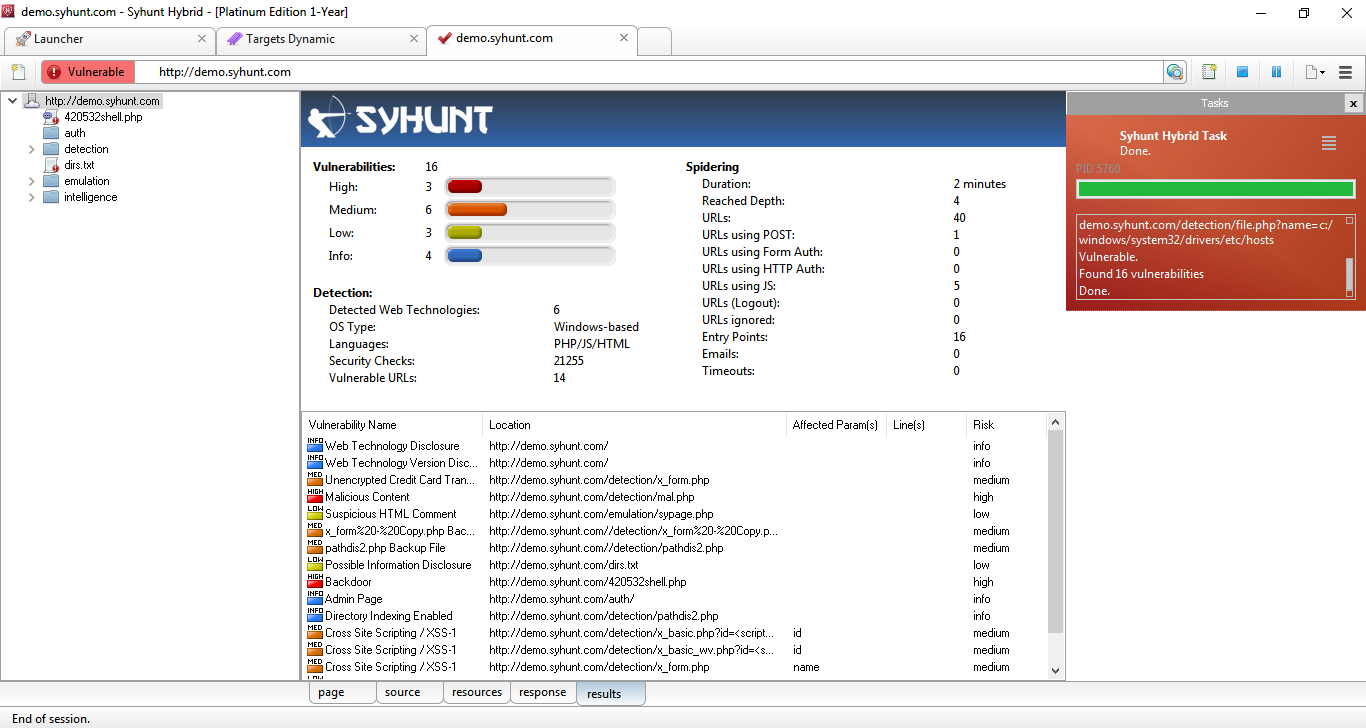
Syhunt Dynamic's UI while a demo scan is in progress
New Fingerprinting Capabilities
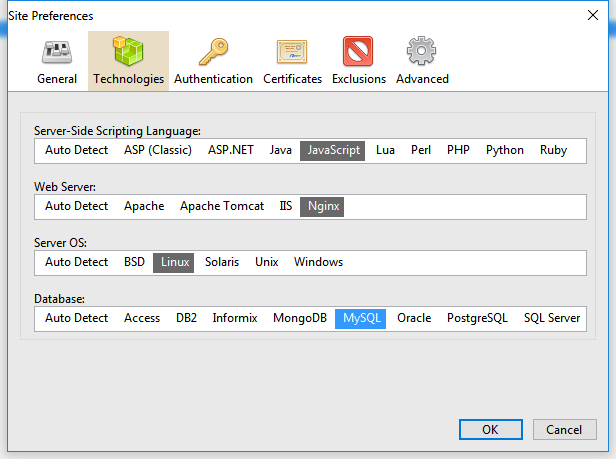
Because of the so many vulnerability checks and mutations added to this version, we developed an advanced and automated fingerprinter tightly integrated with the crawler that automatically maps all the web site technologies and optimizes a scan - this means that Syhunt Dynamic 6 checks are now executed based on the detected web technologies and platform, saving considerable time. The newly added Technologies tab part of the Site Preferences screen allows, if you prefer, to manually set the server-side scripting language, web server, OS and database for a target web site before starting a scan.
In addition to the changes above, the Checks screen has been revamped to accommodate a large number of newly added checks - you can find a list and details about the new checks at the end of this page as well as a link to the consolidated list of checks.


Four-Step Vulnerability Rating

This release comes with a four-step vulnerability rating (High, Medium, Low, Info). We added the Info risk classification and removed the Minimal risk classification. Vulnerabilities previously marked as Minimal risk were assigned a Low or Info risk depending on each case.
New Hunt Methods
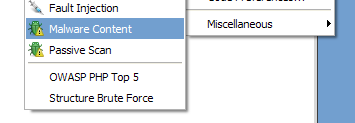
Malware Content - Added to both Syhunt Dynamic and Syhunt Code, allows to scan specifically for malware content, web backdoors, hidden debug parameters and signs of hacking.
Passive Scan - Added to Syhunt Dynamic, allows to scan specifically for Common Exposures, Source Disclosures, Web Technology Disclosures, Suspicious HTML Comments and Malicious Content within a website's surface.
Enhanced Dynamic Scanner
Several important enhancements were made to the spider which is a core part of Syhunt Dynamic:
- Faster and improved HTTP response analysis - improved parsing of web forms, JavaScript code and comments, and added support for additional HTML5 features.
- Added detection of known redundant app patterns.
- Added an option for enabling/disabling the use of Referer in HTTP requests (enabled by default).
- Improved file format and relative path handling.
- Improved cookie and token handling.
- Improved auto form filling, auto login and logout detection (many additional cases covered).
- Improved page redirect handling.
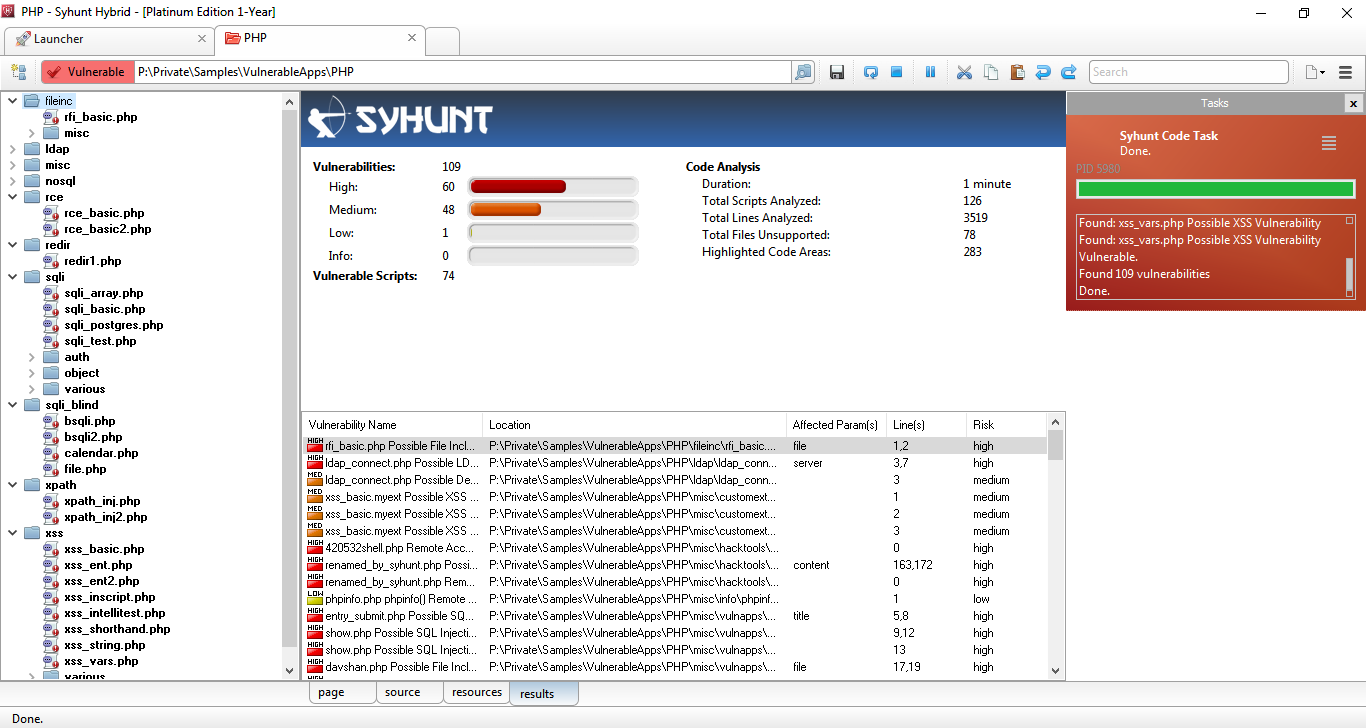
Enhanced Code Scanner
- Significantly faster scans (revised code for scan optimization)
- Improved entry point mapping - Added detection of new entry points in PHP code, allowing additional vulnerability cases to be detected.
- Added automatic file format detection.
- Improved reporting of vulnerable lines
Enhanced Web Browser (Sandcat 6)
- Request Viewer rewrite with better display of requests and important stability fixes
- Simplified the tabbed UI - Major tab code clean up and reorganization.
- Disabled the Chromium's XSS protection - especially useful for performing manual testing or manually confirming XSS detection cases.
New Dynamic Checks
Added detection of many additional vulnerability classes through dynamic application security testing:
- Code Injection in multiple languages - ASP Classic, ASP.NET, Java/JSP, Lua, Perl, PHP, Python, Ruby & Server-Side JavaScript are covered, using both print-based and time-based detection techniques and taking in consideration different web server environments. CWE-94
- Expression Language (EL) Injection in JSP web applications - CWE-917
- XML Injection and XML External Entity (XXE) Injection - CWE-661 and CWE-827
- Authentication Bypass vulnerabilities - CWE-287
- Authentication Brute Force - Both form and HTTP-based, fully automated with common weak passwords
- Debug Parameter Discovery and Injection
- Malicious Content Detection
- Innappropriate Content Detection - Like adult or warez content
- Web Technology Disclosures - Reports if the version of a detected web technology is being disclosed.
Improved the detection of several vulnerability classes:
- SQL Injection - Added additional checks for error-based and time-based SQL Injection, and improved checks for MySQL, MS SQL and PostgreSQL
- NoSQL Injection - Added MongoDB error-based detection
- Remote Command Execution checks - Added time-based detection and new variants
- Directory Traversal checks - Added many new variants and filter evasion techniques
- Cross-Site Scripting (XSS) - Added a subcategory for Client-Side Denial-of-Service
- Web Backdoors - Added 211 new known backdoor checks
- File Inclusion - Added many new variants and improved detection
- Source Code Disclosure - Added new variants covering server-side Lua, PHP and ASP code, and improved accuracy
- LDAP Injection checks - Improved detection
- CRLF Header Injection checks - Added new variants and improved confirmation
- Server-Side Includes Injection checks - Added new variants
- XPath Injection checks - Added new variants and improved confirmation
- HTML Comment checks - Introduced a more advanced parser, added support for JS comments, added several new checks and eliminated false positive cases.
- Backup File Checks - Eliminated a common false positive case.
- Structure Brute Force Checks - Extended many checks to cover web root, added normal and paranoid modes, checks for admin pages now performed as part of the brute force checks.
- Vulnerable Web Apps - Revised checks for known vulnerable web apps divided into multiple categories: Apache Struts, ASP, ASP.Net, Flash, Dynamic HTML, Java, Perl, Python, Ruby, ColdFusion, SSI, IIS...
- Multiple Disclosure checks - Revised checks for multiple disclosure flaws (divided into Path Disclosure, Password Disclosure, Database Disclosure and Information Disclosure). Fixed a case that could result in duplicated Path Disclosure reporting.
- Common Form Weaknesses - Improved checks for multiple form input related vulnerabilities, such as Unencrypted Login, Email Form Hijacking, Hidden Price Form Field and AutoComplete Enabled in sensitive form inputs.
- Common Exposures, Suspicious HTML Comments and Directory Listing checks - Introduced a new, extended check database and eliminated some possibilities of redundant reporting.
New Code Checks
Added detection of many not previously covered vulnerabilities through static application security testing:
- XPath Injection vulnerabilities - CWE-643
- LDAP Injection vulnerabilities in PHP code - CWE-90
- SQL Injection involving object-oriented PHP code
- Web Backdoors in source code
- Debug Parameters
- Common Form Weaknesses
Improved the detection of the following checks:
- Arbitrary File Manipulation checks - Added new PHP variants
- Weak Password Hashing check - Revised and fixed false positive cases
Other Improvements and Bug Fixes
- Added detection of new hacking tools through web server log analysis (Syhunt Insight).
- Scan status now reported as Undetermined if the scan aborted before starting due to any serious connectivity issues (like host not found).
- Re-implemented WAF/IDS evasion and detection in Syhunt Dynamic.
- Fixed: short hunt method options (like as for appscan) not working with the newly introduced CLI app ScanURL.exe. Made it print additional vulnerability details.
- Fixed: location URL in reports including manipulated POST params
We hope you enjoy the new release!
