While performing a standard, dynamic scan (also known as black box) the Syhunt scanner injects data in the web applications and subsequently analyzes the application response in order to determine if the application code is vulnerable to specific web application security attacks.
Performing a scan with Syhunt is very easy:
- Click the Scan button
 in the toolbar.
in the toolbar.
- Assign the Start URL.
- Choose an appropriate Hunt Method.
- Hit OK.
This is often everything you need to perform a scan, see below the details about each step.
Table of contents
Defining targets
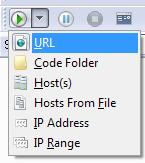
Click the Scan button  in the toolbar and select one of the following options:
in the toolbar and select one of the following options:
URL - You can enter a full URL. Example: http://www.syhunt.com/search.php. If you want to add more than one start URL, see the Start URLs topic.
Host(s) - You can enter a single host or multiple hosts separated by commas. Example: www.host1.com,www.host2.com.
Hosts From File - Allows you to load a list of hosts from a file on your disk.
IP Address - Allows you to enter a numeric IPv4 Address. Depending on the server configuration, you may need to configure a custom virtual host if you use this option (switch to the Hosts sidebar, select or enter the desired IPv4 address and go to Advanced -> Custom Virtual Host.
IP Range - Allows you to enter a IPv4 Range. You may not be able to configure custom virtual hosts if you use this option instead of the normal options.
If your target requires the use of host authentication, you can configure it by switching to the Hosts sidebar.
Starting a scan

The Scan button in the toolbar starts a scan.
Note: If your connection requires the use of a proxy server, you should visit File|Tools|Network Settings.
Monitoring a scan
Click the Events button  in the standard buttons toolbar to see the Events screen. This screen displays information related to the current scan session (scan progress, found vulnerabilities, and more).
in the standard buttons toolbar to see the Events screen. This screen displays information related to the current scan session (scan progress, found vulnerabilities, and more).
Aborting a scan
The Stop button will stop a scan in progress. This button will be grayed if you have not started a scan.
Choosing a hunt method
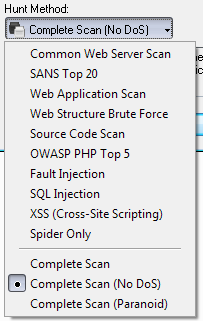
The Complete Scan (No DoS) method is the default scan method in Syhunt. All available scan methods are described below. If you want to use a different scan method, click the Hunt Method button in the standard toolbar. You will be able to select one of the following options:
Common Web Server Scan
Scans for outdated server software, common web server vulnerabilities and exposures. This scan method will not crawl the web site, but look for vulnerabilities in a very similar way to classic (CGI) scanners
SANS Top 20
Scans specifically for the SANS Top Twenty List of Critical Network Vulnerabilities.
Web Application Scan
Identifies flaws in custom web applications. This scan method crawls the web site and performs attacks against the web site structure and the web applications. This includes looking for fault injection vulnerabilities such as XSS, SQL Injection, File Inclusion, and more.
Web Structure Brute Force
A structure brute force will check for:
- Common Vulnerable Scripts
- Common File Checks
- Custom File Checks (User File Checks)
- Database Disclosure
- Web-Based Backdoors
The number of checks is influenced by the number of directories found during the spidering stage.
OWASP PHP Top 5
Scans specifically for the OWASP Top Five List of PHP Vulnerabilities.
Fault Injection
Scans specifically for fault injection vulnerabilities. If this scan method is selected, all other checks that does not require injection are disabled and Syhunt will then specifically check for SQL injection, XSS, file inclusion, and similar flaws.
Cross-Site Scripting (XSS)
Scans specifically for XSS vulnerabilities.
SQL Injection
Scans specifically for SQL & NoSQL Injection vulnerabilities.
Complete Scan
Scans for both common web server vulnerabilities and web application vulnerabilities. This is the combination of the common web server scan and the web application scan methods plus some additional checks. A Complete Scan can sometimes be very time-consuming when performed against a web server that has a large quantity of web folders (eg: 200 or more web folders).
Complete Scan (No DoS)
Same as before, but with denial-of-service tests disabled.
Complete Scan (Paranoid)
Scans for both common web server vulnerabilities, web application vulnerabilities and common vulnerable scripts around the site structure. This scan method can be very time-consuming, specially when executed against large web sites.
Important: Syhunt's web application scan is only activated when one of these scan methods are selected: Web Application Scan, PHP Top 5, Fault Injection, SQL Injection, XSS or Complete Scan. All other scan methods does not include application checks/spidering.
For detailed information about scan methods, see the Hunt Methods page.
Customizing the report
If you want to customize the report, visit Advanced|Reporting & Logging. The General tab allows you to configure a custom report title, font, colors, and more.
Customizing checks
If you want to customize checks, switch to the Checks sidebar. The following options will be available:
Application Checks - Allows you to configure which application tests should be performed. The list includes Common Files, Extension Checking, Path Disclosure, Source Code Disclosure, and more.
Application Checks|Injection - Allows you to configure which fault injection tests should be performed. The list include Command Execution, Cross Site Scripting, Directory Listing, and more.
Server Checks - Allows you to configure which server checks should be performed. The list include ASP, CGI, ColdFusion, Domino, FrontPage, IIS, and more.
Generating a report
The Generate a Report button in the File menu allows you to generate reports (this however will not be possible if you have not started a scan). For detailed information about reports, see the Reports page.
Configuring additional options
The Options sidebar gives you access to general and advanced options.
General
Enable program sounds - If this option is enabled, the scanner will play a sound when a vulnerability is found.
Scan Settings
Use virtual hosts - Only disable this option if your site does not rely on virtual hosts or if you configured a custom virtual host in the Target Settings screen for the target host.
Use browser behaviour - When analyzing web sites there are many situations on which it is better to behave like a web browser and less like a robot. This will often increase the Syhunt's accuracy.
User-Agent - Allows you to configure a custom user-agent. By default, the scanner will identify itself as IE.
Perform reconnaisance - Enables Syhunt to choose the exploits according to the type of web server you are testing, reducing the assessment time.
Use fast CGI scanning method and Use the maximum optimization level - If these options are enabled, Syhunt will constantly try to reduce the assessment time during the scan by optimizing checks. Both options have no impact in the applications scan stage, only in the server scan stage.
Timeout
Pause the scan if there is excessive timeouts - Syhunt will warn if there is excessive timeouts, show recommendations and pause the scan if this option is enabled.
Filters
Filter invalid server responses, Use intelligent filtering and Use anti-redirect filtering - These options have been developed for minimizing false positives and will never limit the depth of the analysis. If you disabled them you may get a few false positives, specially during the server scan stage.
Ignore List
Ignore common unnecessary URL/form parameters and Ignore common unnecessary extensions - These options have been mainly developed for speeding up scans and increase the accuracy of the fault-injection checks. Disabling these options may cause issues while performing crawling and application checks. Both options have no impact in the server scan stage, only in the application scan stage.